Maintain Security Router First Step
When finished with the setting of the required features, network admins often ignore the security side of the router. It would be very risky attack against the router, especially when the router is directly connected to the internet and has a public ip. But make no mistake, the attack against the router does not always come from the Internet, could also originate from the local network. We will try to discuss the first steps that need to be done to keep the router from people who are not responsible.
Services
Mikrotik router running multiple services to facilitate the user in how to access the router, or use other features. The by-default service will be run by the router continuously. We can check the service is run by proxy at the IP menu -> Services
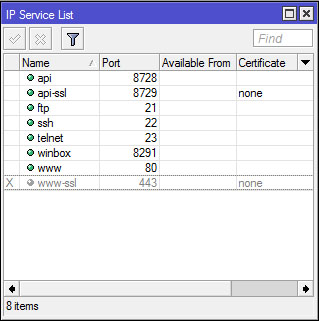
There are several services that run by default mikrotik router. The following information details the MikroTik router service and usefulness.
- API: Application Programmable Interface, a service that allows users to create custom software or applications that communicate with the router, for example to retrieve the information in the router, or even configure the router. Using port 8728.
- API-SSL: It has the same functionality as the API, it's just for the API SSL more secure because it comes with a ssl certificate. API is running SSL using port 8729.
- FTP: FTP Mikrotik provides a standard service that uses ports 20 and 21. Commonly used FTP to upload or download the data router, eg backup files. Authorisation to use the FTP user account and password of the router.
- SSH: remote is one way to secure the router console. Almost the same as telnet, only is more secure because the data is encrypted SSH ditrasmisikan by. MikroTik SSH uses port 22 by default.
- Telnet: It has functions similar to ssh only has a few limitations and a low level of security. Usually used as a router for remote console. MikroTik telnet service uses port 23.
- Winbox: Service that allows connection to the router Winbox application. Of course we are familiar with the Winbox application that is used to remotely graphically router. Winbox connection using port 8291.
- WWW: In addition to the remote console and Winbox, the proxy also provides a means of access via a web-base router using a browser. Ports used are standard HTTP port, which is port 80.
- WWW-SSL: Same as the WWW service that allows access to the router using the web-base, www-ssl but it is more secure because it uses SSL certificae to establish a connection between the router and client that will perform remote. By default it uses port 443.
Next is the question for the network administrator, whether then all of them will be used?.
Sometimes network admins do not really care, service is still running
when not needed, so that the service can be used by people who are not
responsible at all times. Have you ever opened a terminal MikroTik router then appear notice "failure for user root from xx.xx.x.xxx via ssh"? The error informs that a user tries to access the router by guessing the username and password of the router.
Disable Service
To minimize user trying to access the router using a particular
service, the network administrator can turn off services that are found
to be used.
Suppose we just need memngakses router via winbox and web-base, then we
can turn off the service in addition to two earlier services.
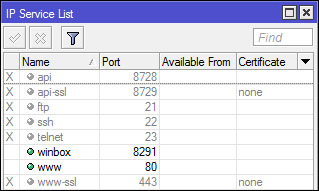
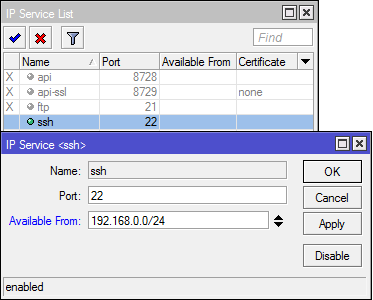
Available From
The network administrator can restrict which network routers can be
accessed on a particular service by specifying the parameter "Available
From" in the service setting. to determine the "Available From", then the service can only be accessed from a specified network. When someone tries to access the router from outside the network-address allowed, will automatically be rejected by the router. Parameters "Available From" can be filled with the IP address or network address.
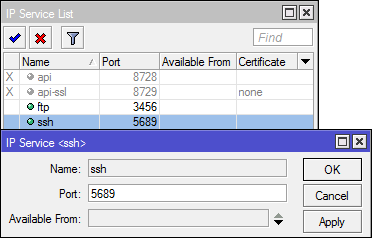
Change Port
In addition to determining the allowed addresses, network administrators can also change the port used by a particular service. A person working in the world of networking can easily guess the default port used by the service - limited service.
User Management
Some administrators sometimes think that by giving a password alone is enough.
Then to share your username and password to some fellow technicians,
even for technicians who only have access router monitoring also granted
admin permissions. It would be very risky when the router is a router that is handled is important. Here are some tips wise user management.
Group Policies
Technicians who only have the responsibility of monitoring the network does not require full access rights to the router. Usually full access rights are owned only by the person most knowledgeable about the condition and configuration of the router.
Network administrator can create a user in accordance with their job
responsibilities - each with the group and determining policies on user
settings. If using Winbox, go to System -> Users -> Tab Group.
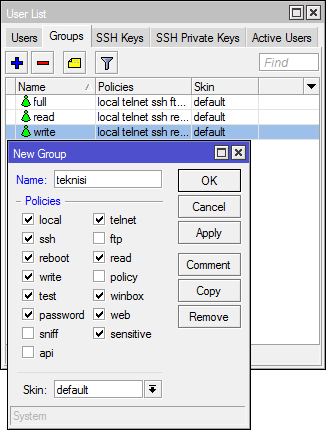
There are several policy options that will be given to determine the user privilege. The following details the policy options and rights held:
- local: a policy that allows the user login via the local console (keyboard, monitor)
- telnet: use policies that allow remote login via telnet
- ssh: policies that allow the user to log in remotely via secure shell protocol
- ftp: Policies that allow login via FTP full rights, including the dar file transfer to / from the router. Users with this policy have the right read, write, and delete files.
- reboot: Policies that allow the user to restart the router.
- read: Policies that allow to see the router configuration. All console command that is not accessible configuration.
- write: Policies that allow to configure the router, except for user management. This policy does not allow the user to read the configuration of the router, the user is given wirte policy is also given policy is also recommended read.
- policy: The policy for the management of user rights meemberikan. Should be used together with write policy. Allows also to see the global variables created by other users (requires also 'test' policy).
- test: Policies that give the right to run ping, traceroute, bandwidth-test, wireless scan, sniffer, snooper and test other commands.
- Web: Policies that give the right to a remote router via WebBox
- Winbox: Policies that give the right to a remote router via WinBox
- password: Policies that give the right to change passwords
- sensitive: policy which entitles the router to see sensitive information, such as secret radius-key authentication, etc..
- Fire: Policies that give the right to a remote router via the API.
- Sniff: Policies that give the right to use a packet sniffer tool.
"Allowed Address" is used to determine which network the user is allowed access to the router.
Suppose the network admin has a policy that technicians may only
mengankses router via a local network, should not be through the public
network. in such cases, we can use the option "Allowed Address".
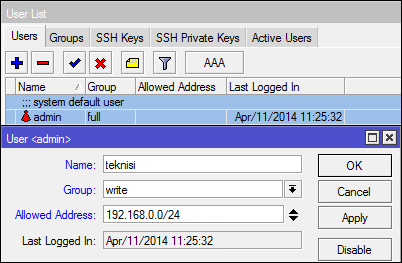
Allowed to address the ip address or network addresss.
If we are content with the ip address, then the user can only login
when using a particular IP address, if we fill the network address, the
user can be used to segment a specific Ip address.
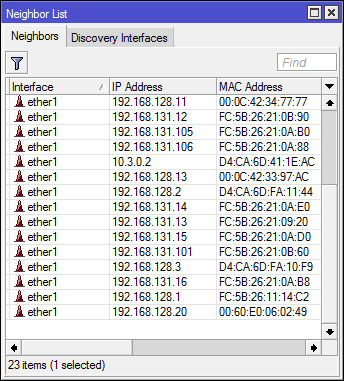
MikroTik Neighbor Discovery Protocol (MNDP)
Is a Layer 2 broadcast domain that allows devices that support MNDP or CDP for each "find". The simplest example when we scan Winbox to the router remotely. By performing a scan, will appear mac address information, identity, and the ip address of the router. So when this MNDP running, users in the network, the router can easily find the router, and the router knows some information. In Mikrotik routers, routers that are running can be seen in the menu MNDP IP -> Neighbors. It would seem that the router was connected and running MNDP.
So that the router does not display information when a user scans
discovery protocols, network administrators are advised to disable
discovery interface. If using Winbox, go to IP -> neighboor -> Tab Discovery Interfaces.
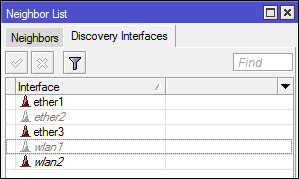
For example, we disable the setting ether2 discovery interfaces, the
router can not be scanned or "found" on the network that is connected to
ether2.
No comments:
Post a Comment