MikroTik combination with External Proxy
Proxy not a stranger in the world of Mikrotik. Mikrotik itself has proxy feature that can be quite simple. Many users Mikrotik then add external proxy in order to use features that are more complex than internal features of proxy. The question is, whether they have a significant performance difference? In this article we will try to do test the performance of internal and external proxy. |
Configuring External Proxy with MikroTik
To test this, we will use an external application proxy that is commonly used, namely Squid. Step-by-step installation and configuration of the application of this squid can we get references on the internet. And do not worry a lot of references that have been using the Indonesian language for this application many users even in Indonesia.
After installation and configuration of Squid is complete, then we will do the setting transparent proxy. This works for all traffic accessing the HTTP (TCP Protocol, Port 80) is deflected into the Proxy server. Configuration of the transparent proxy this we will do in the MikroTik Router using NAT Firewall feature. The steps are as follows:
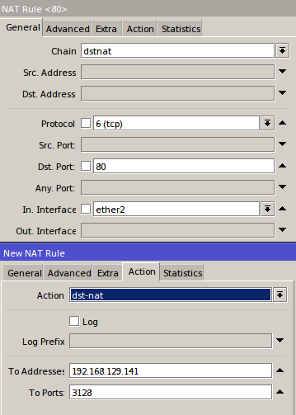
Go to the menu IP -> Firewall -> Nat -> click the Add [+]. Then specify the parametersChain, Protocol, Dst.Port, in accordance with the above view. In a special parameter.Interface stay we adjust the link that leads to a local network. Furthermore, the Tab Action, Action parameters for use dst-nat and we also specify the parameters To Addresses and Ports To address the Proxy server and the port used. In this example the proxy server using the IP address and the port is 192 168 129 141 3128.
Now, with the above step has been formed transparent proxy. Next we will do test whether the configuration that we have done goes well or not. We will try to access the website we have added to the list 'Blocking' on the Proxy server.
Now, with the above step has been formed transparent proxy. Next we will do test whether the configuration that we have done goes well or not. We will try to access the website we have added to the list 'Blocking' on the Proxy server.
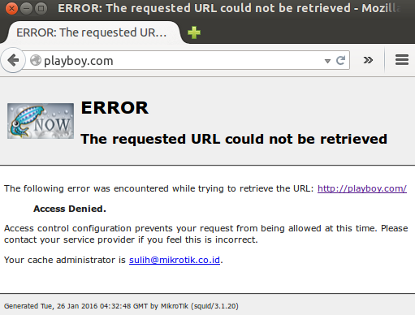
If the error text is displayed as described above, the configuration we have been successful.
Internal configuration MikroTik Proxy (Web Proxy)
After we tried to use the External Proxy, now we'll try to feature contained in the Proxy MikroTik. As we have seen MikroTik adding a feature that can be used to perform the access management of user / client. Such features are Web Proxy. How the steps to configure this feature can be seen in the discussion of the previous article here .
Internal configuration MikroTik Proxy (Web Proxy)
After we tried to use the External Proxy, now we'll try to feature contained in the Proxy MikroTik. As we have seen MikroTik adding a feature that can be used to perform the access management of user / client. Such features are Web Proxy. How the steps to configure this feature can be seen in the discussion of the previous article here .
On these links already explained how we enable and also setting the web proxy feature is that access a web page can be set here. And on the link it has also been described how to create a transparent proxy to redirect traffic to Web Proxy feature. For transparent proxy is also the same as we have done before, but the difference here is the selection of parameters Action. If we use the Internal Proxy (Web Proxy), the action we have set with the option 'Redirect' because the system proxy server located at localhost (router).Meanwhile, if we use the External Proxy (Squid), the action we have chosen is 'dst-nat'.
Well, if Inetrnal proxy configuration (Web Proxy) we have done, now we will try to access the web that we have entered kedaftar 'Deny' in the Web Proxy. As before, if the configuration we are going well or not.
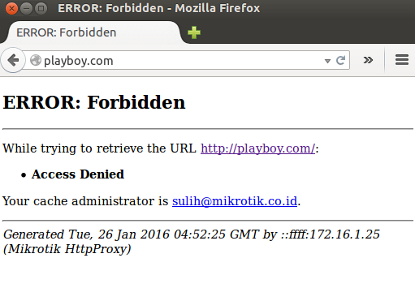
Well, if Inetrnal proxy configuration (Web Proxy) we have done, now we will try to access the web that we have entered kedaftar 'Deny' in the Web Proxy. As before, if the configuration we are going well or not.

And if it displays an error on the web browser as above, then the web proxy configuration has been successful.
Performance Test (Pros & Cons)
Performance Test (Pros & Cons)
Once we tried to configure and implement the above two types of proxy servers, we can make the performance of each proxy server. To perform the analysis of the performance of the proxy, there beberpa tool that we can use. Among such Grinder, Gatling, Tsung,Apache JMeter. The tools we can get it for free and also the configuration steps in the application developer's website.
This time we will try the application Tsung to analyze the performance of proxy that we have built before.
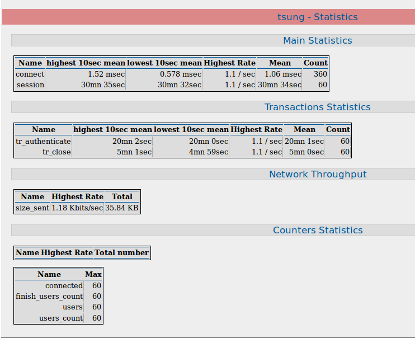
Well, from here we can draw a conclusion as to the performance of each proxy server.Where, for the use of simple, both the proxy server is not too much different, but to side configuration External Proxy (Squid) more custom.
:: Internal Proxy (Web Proxy) ::
:: External Proxy (Squid) ::
This time we will try the application Tsung to analyze the performance of proxy that we have built before.


With these tools we can see the performance of the proxy server to view a table or graph.There beberpa parameters to be analyzed seeprti Response Times, Network Throughput, Transactions Statistics, Counter Statistics.
Well, from here we can draw a conclusion as to the performance of each proxy server.Where, for the use of simple, both the proxy server is not too much different, but to side configuration External Proxy (Squid) more custom.
:: Internal Proxy (Web Proxy) ::
- Easy installation process.
- Easy to configure (there are GUI display).
- If the size of storage on a small router, then it's not recommended to enable proxy caching feature, or at least not only used to cache small files.
:: External Proxy (Squid) ::
- Easy to install, simply add NAT Mikrotik side.
- A little tricky to configuration (must use scripting).
- Suitable for more advanced needs.
- The storage capacity is relatively large, because the use of a PC so that the proxy cache feature can run optimally
